Checkpoints
Deploy sample App Engine application
/ 100
Web Security Scanner: Qwik Start
GSP112
Overview
The Web Security Scanner, one of Security Command Center's built-in services, identifies security vulnerabilities in your Google App Engine, Google Kubernetes Engine (GKE), and Compute Engine web applications. It crawls your application, following all links within the scope of your starting URLs, and attempts to exercise as many user inputs and event handlers as possible.
The scanner is designed to complement your existing secure design and development processes. To avoid distracting developers with false positives, the scanner errs on the side of under reporting and will not display low confidence alerts. It does not replace a manual security review, and it does not guarantee that your application is free from security flaws.
Setup
Before you click the Start Lab button
Read these instructions. Labs are timed and you cannot pause them. The timer, which starts when you click Start Lab, shows how long Google Cloud resources will be made available to you.
This hands-on lab lets you do the lab activities yourself in a real cloud environment, not in a simulation or demo environment. It does so by giving you new, temporary credentials that you use to sign in and access Google Cloud for the duration of the lab.
To complete this lab, you need:
- Access to a standard internet browser (Chrome browser recommended).
- Time to complete the lab---remember, once you start, you cannot pause a lab.
How to start your lab and sign in to the Google Cloud console
-
Click the Start Lab button. If you need to pay for the lab, a pop-up opens for you to select your payment method. On the left is the Lab Details panel with the following:
- The Open Google Cloud console button
- Time remaining
- The temporary credentials that you must use for this lab
- Other information, if needed, to step through this lab
-
Click Open Google Cloud console (or right-click and select Open Link in Incognito Window if you are running the Chrome browser).
The lab spins up resources, and then opens another tab that shows the Sign in page.
Tip: Arrange the tabs in separate windows, side-by-side.
Note: If you see the Choose an account dialog, click Use Another Account. -
If necessary, copy the Username below and paste it into the Sign in dialog.
{{{user_0.username | "Username"}}} You can also find the Username in the Lab Details panel.
-
Click Next.
-
Copy the Password below and paste it into the Welcome dialog.
{{{user_0.password | "Password"}}} You can also find the Password in the Lab Details panel.
-
Click Next.
Important: You must use the credentials the lab provides you. Do not use your Google Cloud account credentials. Note: Using your own Google Cloud account for this lab may incur extra charges. -
Click through the subsequent pages:
- Accept the terms and conditions.
- Do not add recovery options or two-factor authentication (because this is a temporary account).
- Do not sign up for free trials.
After a few moments, the Google Cloud console opens in this tab.

Activate Cloud Shell
Cloud Shell is a virtual machine that is loaded with development tools. It offers a persistent 5GB home directory and runs on the Google Cloud. Cloud Shell provides command-line access to your Google Cloud resources.
- Click Activate Cloud Shell
at the top of the Google Cloud console.
When you are connected, you are already authenticated, and the project is set to your Project_ID,
gcloud is the command-line tool for Google Cloud. It comes pre-installed on Cloud Shell and supports tab-completion.
- (Optional) You can list the active account name with this command:
- Click Authorize.
Output:
- (Optional) You can list the project ID with this command:
Output:
gcloud, in Google Cloud, refer to the gcloud CLI overview guide.
Task 1. Before you begin, you need an app to scan
In this lab, you will deploy a sample Hello World application to run Security Scanner on.
- Run the following command in Cloud Shell to clone the Hello World sample app repository:
- Then go to the directory that contains the sample code:
- Change the python version with the sed command.
- Run the below command and add
itsdangerous==2.0.1,Jinja2==3.0.3andwerkzeug==2.0.1in the requirements.txt file:
so that the file looks like:
- Save the file (press Ctrl+O then Enter) and exit nano (press Ctrl+X).
itsdangerous==2.0.1 is added in requirements.txt file to safely pass data to untrusted environments and get it back safe.Task 2. Test app
- Installing Prerequisites Python environment.
- From within the
hello_worlddirectory where the app's app.yaml configuration file is located, start the local development server with the following command:
- The local development server is now running and listening for requests on port 8080. Click on the web preview button in Cloud Shell, and select Preview on port 8080 to see it:
- Press Ctrl+c to stop the local app and return to the command line.
Task 3. Deploy app
In this lab use
- Deploy your app to App Engine by running the following command from within the root directory of your application (
hello_world):
-
You'll be asked to select a region. Choose the number for one that is near where you are.
-
After the app is created in your lab, you'll be asked if you want to continue. Click Y to continue.
Deployment of your app will then begin.
Task 4. View app
- To launch the app in your browser, run the following command:
There will be a link in Cloud Shell that you can use, or view the app at http://[YOUR_PROJECT_ID].uc.r.appspot.com. This is the URL you'll scan for vulnerabilities and it will be added to your scan parameters in the next step.
Test completed task
Click Check my progress to verify your performed task. If you have completed the task successfully you will be granted with an assessment score.
Task 5. Run the scan
The scan does not run immediately, but is queued for later execution; it can take hours before the scan executes, depending on current load. For more information about these form settings, refer to Using Web Security Scanner.
-
Go to Navigation menu > APIs & Services > Library.
-
In Search for APIs & Services type Web Security Scanner.
-
Select the Web Security Scanner API then Click Enable to enable the API.
-
From the Navigation menu select Security > Web Security Scanner.
-
Click New Scan.
-
Under
Starting URL 1, enter the URL of the application you want to scan. -
Click Save to create the scan.
-
Click Run to start scanning:
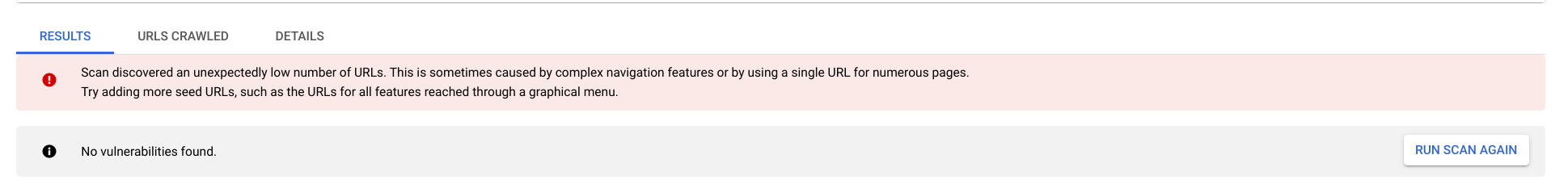
The scan will be queued, and you can watch the status bar progress as it scans. The scan overview page displays a results section when the scan completes. The following image shows example scan results when no vulnerabilities are detected:
Nice job! You just completed a scan using Web Security Scanner. You will see a warning to let you know that only scanning 1 URL isn't ideal. This lab is just to demonstrate a simple example. Your production environment will have plenty of URLs to scan.
Task 6. Test your understanding
Below is a multiple-choice question to reinforce your understanding of this lab's concepts. Answer it to the best of your abilities.
Congratulations!
Finish your quest
This self-paced lab is part of the Baseline: Deploy & Develop and Security & Identity Fundamentals quests. A quest is a series of related labs that form a learning path. Completing this quest earns you a badge to recognize your achievement. You can make your badge or badges public and link to them in your online resume or social media account. Enroll in any quest that contains this lab and get immediate completion credit. See the Google Cloud Skills Boost catalog to see all available quests.
Next steps / learn more
This lab is also part of a series of labs called Qwik Starts. These labs are designed to give you a little taste of the many features available with Google Cloud. Search for "Qwik Starts" in the lab catalog to find the next lab you'd like to take!
Google Cloud training and certification
...helps you make the most of Google Cloud technologies. Our classes include technical skills and best practices to help you get up to speed quickly and continue your learning journey. We offer fundamental to advanced level training, with on-demand, live, and virtual options to suit your busy schedule. Certifications help you validate and prove your skill and expertise in Google Cloud technologies.
Manual Last Updated July 25, 2024
Lab Last Tested July 25, 2024
Copyright 2024 Google LLC All rights reserved. Google and the Google logo are trademarks of Google LLC. All other company and product names may be trademarks of the respective companies with which they are associated.